Leakage signal classification and recognition method based on fusion features
-
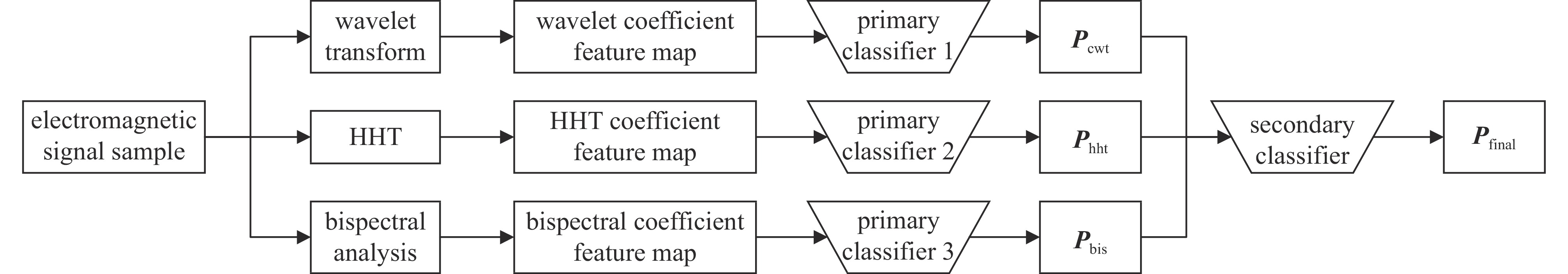
摘要: 随着移动通信、物联网、车联网、工业互联网等网络的发展,电磁环境日益复杂,非法电子设备也日渐增多,各类信号耦合互调现象严重,这给泄漏信号类型识别带来了难题。提出基于融合特征的泄漏信号分类识别方法,综合运用高维度特征提取方法和图形化降维表征方法,结合残差网络等深度学习模型与特征融合分析方法,能够更综合地区分多类电磁泄漏信号,特征抗噪声鲁棒性高,方法可解释性好,可支撑基于电磁信号类型识别的辐射源智能检测工程应用。Abstract: With the development of networks such as mobile communications, Internet of Things (IoT), V2X (meaning Vehicle to everything, including Vehicle to Vehicle and Vehicle to Infrastructure), and Industrial Internet of Things (IIoT), the electromagnetic environment is becoming increasingly complex, illegal electronic devices are also increasing day by day, and there are severe coupling and intermodulation of various signals, which bring difficulties to the identification of leaked signal types. This paper proposes a leakage signal classification and recognition method based on fused features. Comprehensively utilizing high-dimensional feature extraction methods and graphical dimensionality reduction characterization methods, and combining with deep learning models such as residual networks and feature fusion analysis methods, the method can distinguish more comprehensively multiple types of electromagnetic leakage signals. The features method has with high robustness against noise and good interpretability, and can support the intelligent detection engineering application of radiation sources based on electromagnetic signal type recognition.
-
表 1 五类泄漏源
Table 1. Five types of leakage sources
No. signal type total sampling points
of each WAV filenumber of samples
intercepted by each WAV filetotal number of
samples taken1 clock leak signal 11264000,10035200, 7168000 ,7782400 563,501,358,389 1811 2 laptop touchpad leak signal 12247040,15589376, 17924096,21274624 612,779,896,1063 3350 3 environmental radio
emissions signal17981440,22003712,25976832, 25075712 ,15302656 899,1100,1298,1253,765 5315 4 screen display signal 21553152,34586624,26722304 1077,1729,1336 4142 5 unknown radiation source signal 15728640,17661952, 26402816,16826368 786,883,1320,841 3830 表 2 五类泄漏源特征
Table 2. Five types of leak source characteristics
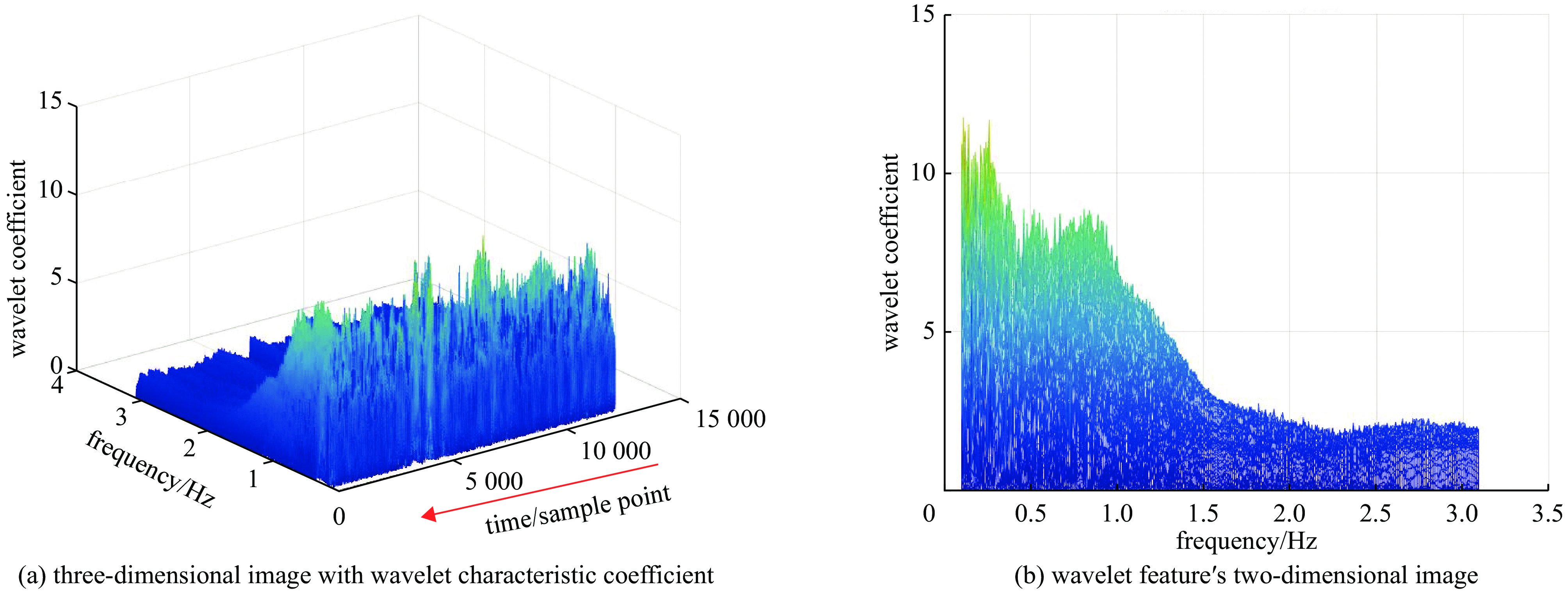
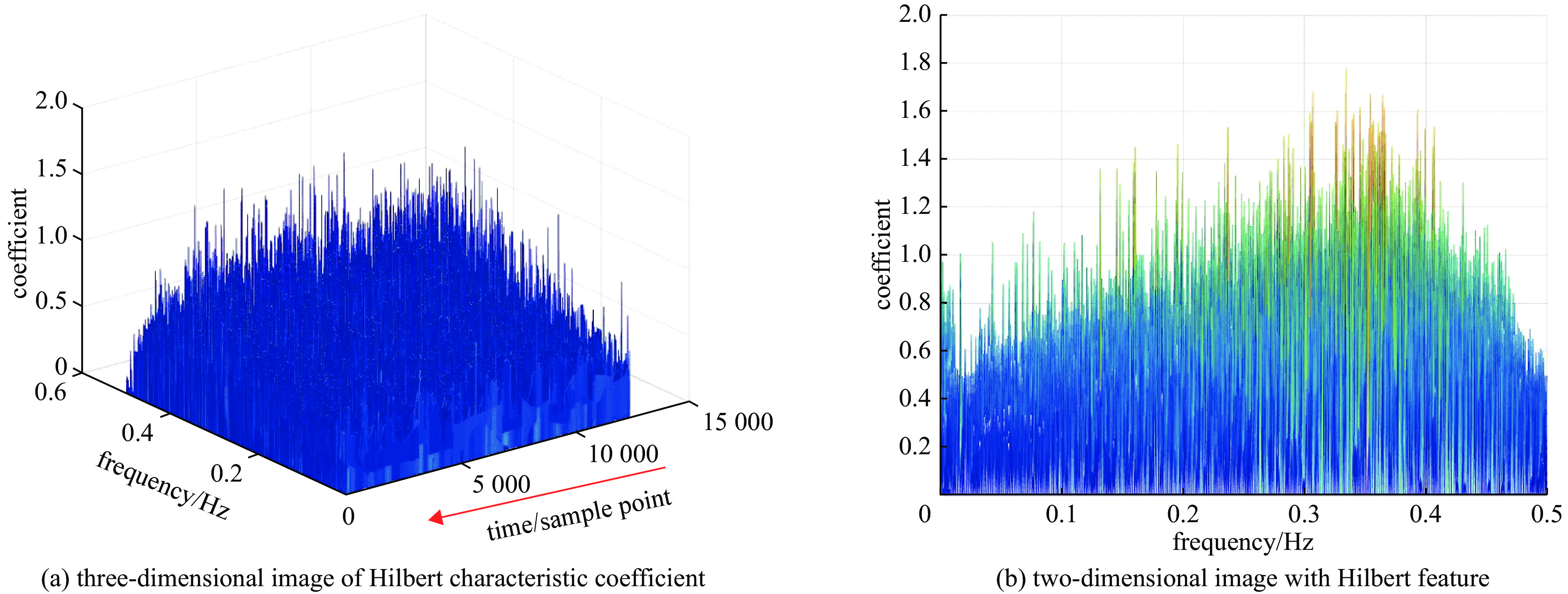
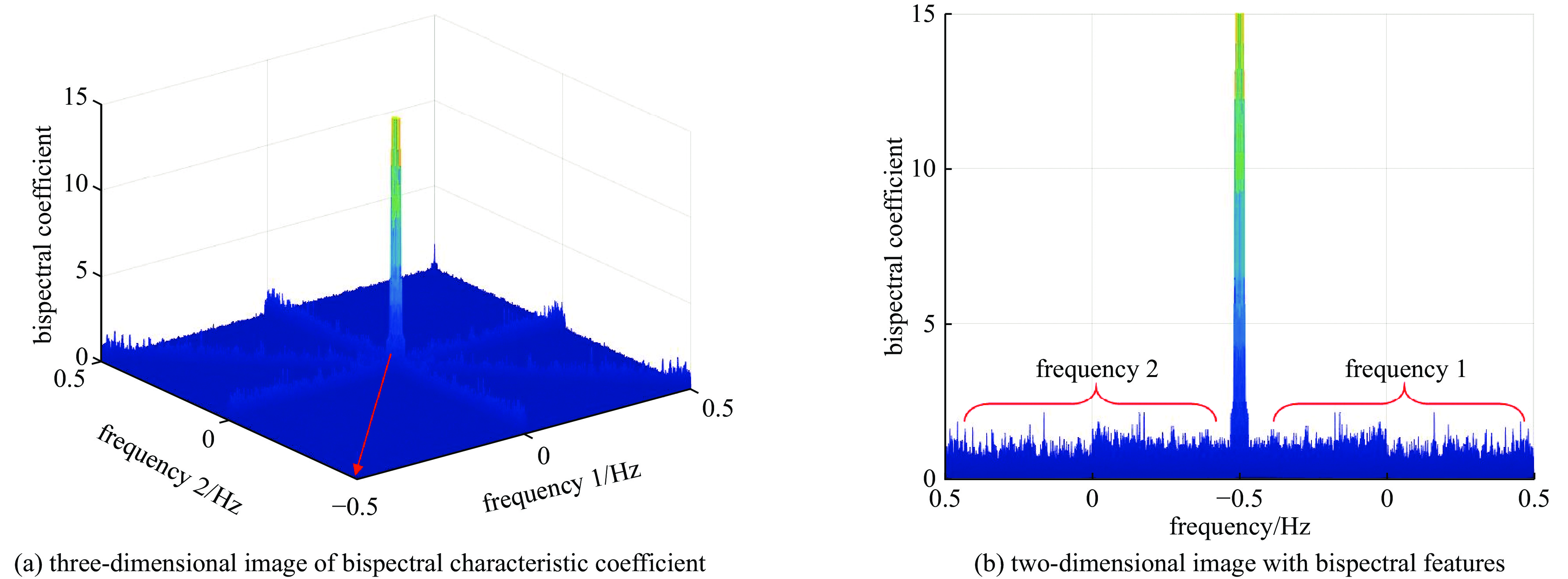
No. signal type wavelet feature map HHT feature map bispectral feature map 1 clock leak signal 


2 laptop touchpad
leak signal


3 environmental radio
emissions signal


4 screen display signal 


5 unknown radiation
source signal


表 3 五类泄漏源样本数据集数量
Table 3. Number of sample data sets of five types of leakage sources
No. signal type balanced dataset sample size unbalanced dataset sample size training set test set training set test set 1 clock leak signal 1440 360 1449 362 2 laptop touchpad leak signal 1440 360 2680 670 3 environmental radio emissions signal 1440 360 4252 1063 4 screen display signal 1440 360 3313 829 5 unknown radiation source signal 1440 360 3064 766 表 4 不同信噪比下的不同特征图预测准确率
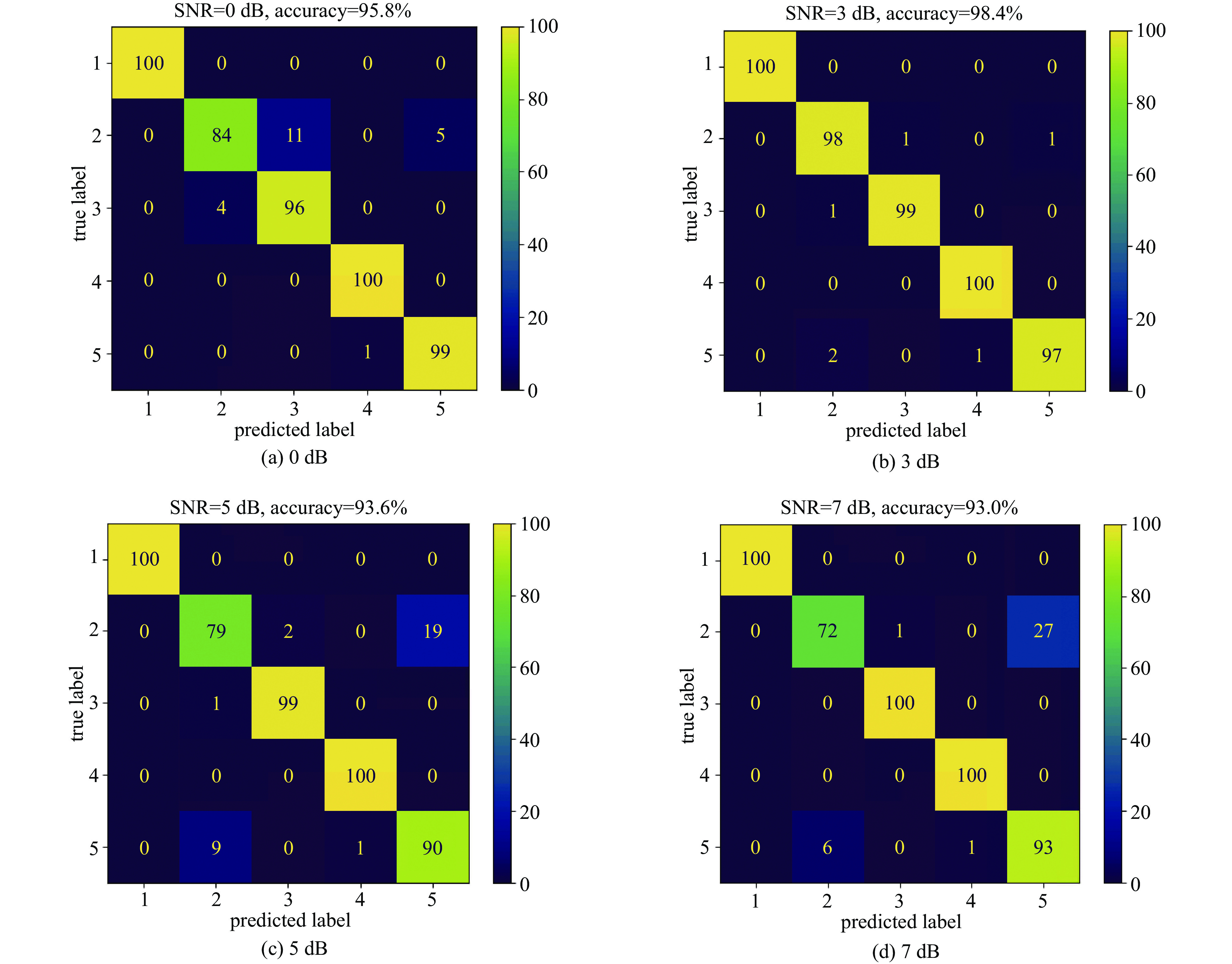
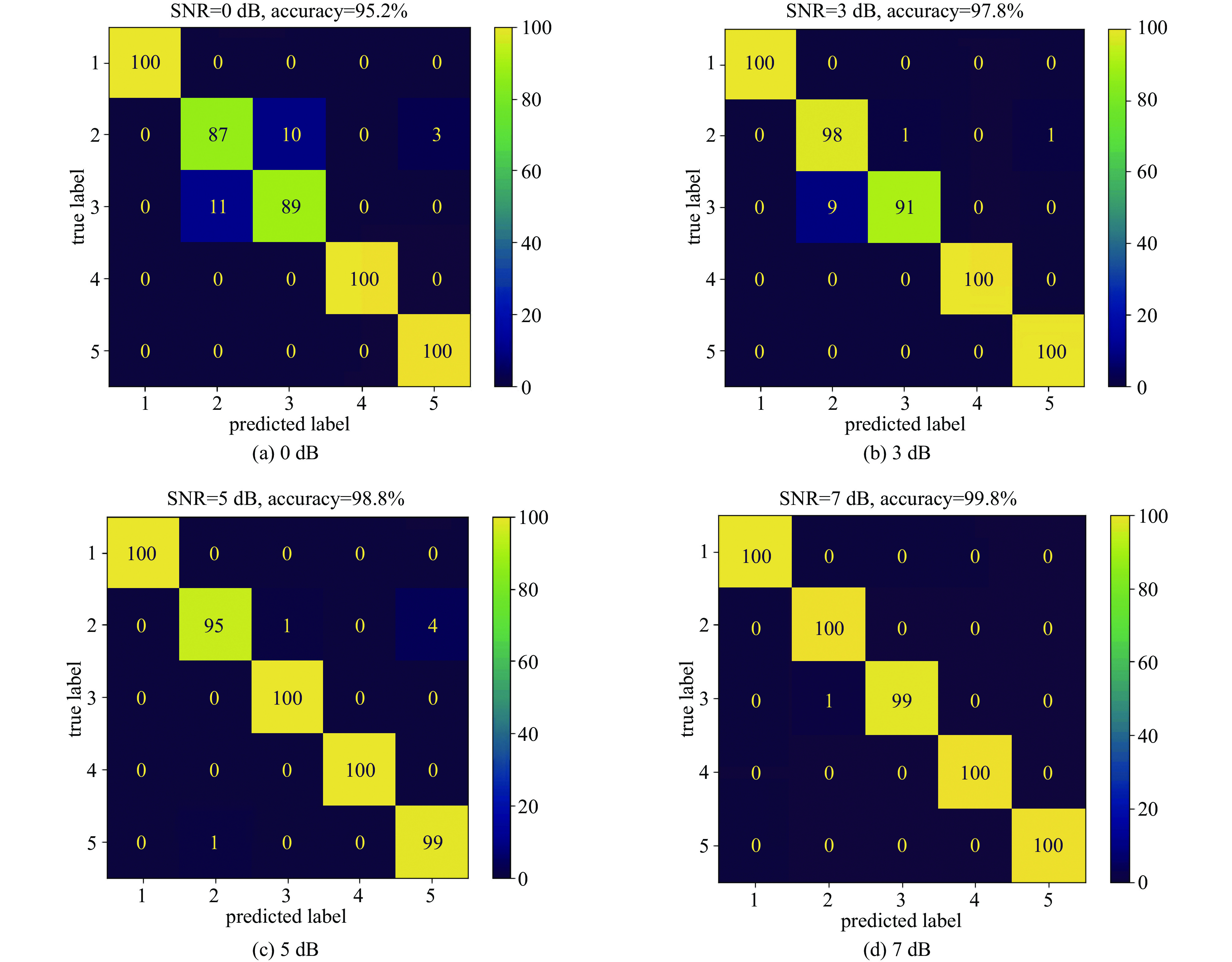
Table 4. Prediction accuracy of different feature maps under different signal-to-noise ratios
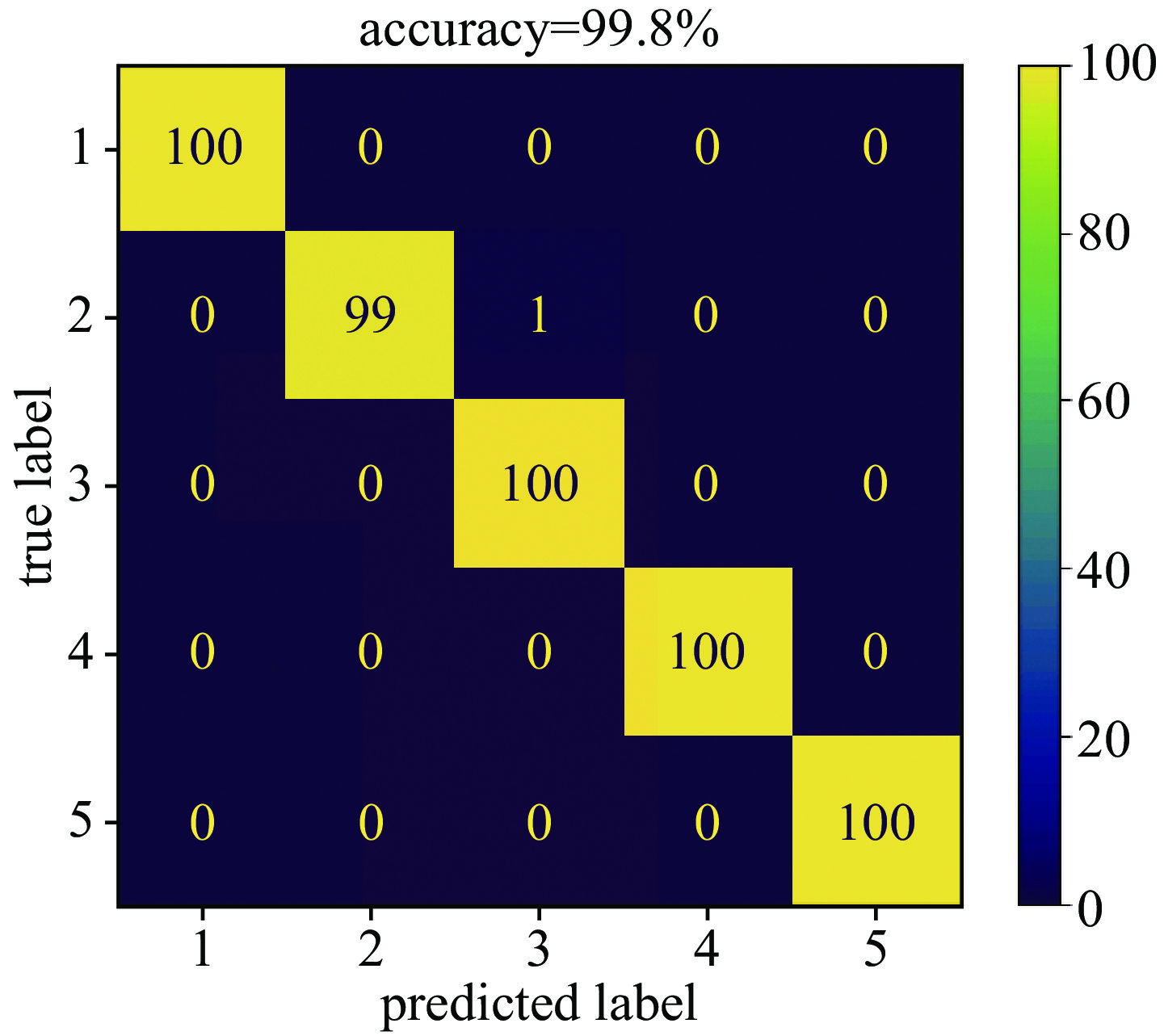
No. SNR/dB fusion feature map/% wavelet feature map/% HHT feature map/% bispectral feature map/% 1 0 99.8 95.8 95.2 100 2 3 100 98.4 97.8 100 3 5 100 93.6 98.8 100 4 7 100 93.0 99.8 100 -
[1] 刘文斌, 丁建锋, 寇云峰, 等. 物理隔离网络电磁漏洞研究[J]. 强激光与粒子束, 2019, 31:103215 doi: 10.11884/HPLPB201931.190132Liu Wenbin, Ding Jianfeng, Kou Yunfeng, et al. Research on electromagnetic vulnerability of air-gapped network[J]. High Power Laser and Particle Beams, 2019, 31: 103215 doi: 10.11884/HPLPB201931.190132 [2] 刘文斌, 王梦寒, 寇云峰, 等. 基于电磁泄漏信号的电子设备行为识别与安全应用[J]. 通信技术, 2019, 52(7):1761-1765 doi: 10.3969/j.issn.1002-0802.2019.07.038Liu Wenbin, Wang Menghan, Kou Yunfeng, et al. Behavior recognition and security application of electronic equipment based on electromagnetic leakage signal[J]. Communications Technology, 2019, 52(7): 1761-1765 doi: 10.3969/j.issn.1002-0802.2019.07.038 [3] 刘文斌, 丁建锋, 寇云峰, 等. 软件定义电磁泄漏技术与应用分析[J]. 通信技术, 2017, 50(9):2094-2099 doi: 10.3969/j.issn.1002-0802.2017.09.035Liu Wenbin, Ding Jianfeng, Kou Yunfeng, et al. Software-defined electromagnetic leakage technology and its application[J]. Communications Technology, 2017, 50(9): 2094-2099 doi: 10.3969/j.issn.1002-0802.2017.09.035 [4] 王梦寒, 寇云峰, 刘文斌, 等. 计算机网络电磁泄漏信号的实时监测与智能识别[J]. 通信技术, 2019, 52(7):1755-1760 doi: 10.3969/j.issn.1002-0802.2019.07.037Wang Menghan, Kou Yunfeng, Liu Wenbin, et al. Real-time monitoring and intelligent recognition of electromagnetic leakage signals in computer networks[J]. Communications Technology, 2019, 52(7): 1755-1760 doi: 10.3969/j.issn.1002-0802.2019.07.037 [5] 关天敏, 韩振中, 茅剑. 显示器电磁信息泄漏的机器学习检测方法研究[J]. 信息安全学报, 2021, 6(2):101-109 doi: 10.19363/J.cnki.cn10-1380/tn.2021.03.07Guan Tianmin, Han Zhenzhong, Mao Jian. Research on the detection method of electromagnetic information leakage from display by machine learning[J]. Journal of Cyber Security, 2021, 6(2): 101-109 doi: 10.19363/J.cnki.cn10-1380/tn.2021.03.07 [6] 徐艳云, 张萌, 黄伟庆. 信息设备电磁辐射信息泄漏的可检测距离估计方法研究[J]. 信息安全学报, 2020, 5(1):44-56 doi: 10.19363/J.cnki.cn10-1380/tn.2020.01.05Xu Yanyun, Zhang Meng, Huang Weiqing. Study on detectable distance for electromagnetic information leakage of information equipment[J]. Journal of Cyber Security, 2020, 5(1): 44-56 doi: 10.19363/J.cnki.cn10-1380/tn.2020.01.05 [7] Sehatbakhsh N, Nazari A, Alam M, et al. REMOTE: robust external malware detection framework by using electromagnetic signals[J]. IEEE Transactions on Computers, 2020, 69(3): 312-326. doi: 10.1109/TC.2019.2945767 [8] Werner F T, Yilmaz B B, Prvulovic M, et al. Leveraging EM side-channels for recognizing components on a motherboard[J]. IEEE Transactions on Electromagnetic Compatibility, 2021, 63(2): 502-515. doi: 10.1109/TEMC.2020.3016892 [9] Jorgensen E J, Werner F T, Prvulovic M, et al. Deep learning classification of motherboard components by leveraging EM side-channel signals[J]. Journal of Hardware and Systems Security, 2021, 5(2): 114-126. doi: 10.1007/s41635-021-00116-2 [10] 丁建锋, 刘文斌, 丁磊, 等. 基于主动检测的电子设备电磁信息泄漏新型威胁分析[J]. 通信技术, 2018, 51(4):936-940 doi: 10.3969/j.issn.1002-0802.2018.04.035Ding Jianfeng, Liu Wenbin, Ding Lei, et al. New threat analysis of electromagnetic information leakage in electronic equipment based on active detection[J]. Communications Technology, 2018, 51(4): 936-940 doi: 10.3969/j.issn.1002-0802.2018.04.035 [11] 丁建锋, 刘文斌, 王梦寒, 等. 计算机声光电磁信号互调泄漏威胁分析[J]. 通信技术, 2019, 52(4):967-970 doi: 10.3969/j.issn.1002-0802.2019.04.034Ding Jianfeng, Liu Wenbin, Wang Menghan, et al. Threat analysis of computer information leakage in intermodulation of acoustic, optical and electromagnetic signals[J]. Communications Technology, 2019, 52(4): 967-970 doi: 10.3969/j.issn.1002-0802.2019.04.034 [12] 程磊, 罗儒俊, 寇云峰, 等. 基于电源线的传导电磁信息泄漏模型与验证[J]. 通信技术, 2018, 51(4):941-946 doi: 10.3969/j.issn.1002-0802.2018.04.036Cheng Lei, Luo Rujun, Kou Yunfeng, et al. Verification of conductive electromagnetic information leakage model based on power line[J]. Communications Technology, 2018, 51(4): 941-946 doi: 10.3969/j.issn.1002-0802.2018.04.036 [13] 齐国雷, 寇云峰, 胡浩, 等. 基于隐蔽声通道的物理隔离计算机信息泄漏研究[J]. 通信技术, 2018, 51(3):700-704 doi: 10.3969/j.issn.1002-0802.2018.03.036Qi Guolei, Kou Yunfeng, Hu Hao, et al. Information leakage based on acoustic convert channel for air-gapped computers[J]. Communications Technology, 2018, 51(3): 700-704 doi: 10.3969/j.issn.1002-0802.2018.03.036 [14] 胡浩, 罗儒俊, 齐国雷, 等. 基于LED显示屏的隐蔽光传输通道[J]. 通信技术, 2018, 51(7):1689-1693 doi: 10.3969/j.issn.1002-0802.2018.07.032Hu Hao, Luo Rujun, Qi Guolei, et al. Covert-optical transmission channel based on LED display[J]. Communications Technology, 2018, 51(7): 1689-1693 doi: 10.3969/j.issn.1002-0802.2018.07.032 [15] Guri M, Zadov B, Bykhovsky D, et al. PowerHammer: Exfiltrating data from air-gapped computers through power lines[J]. IEEE Transactions on Information Forensics and Security, 2020, 15: 1879-1890. doi: 10.1109/TIFS.2019.2952257 -



 下载:
下载: